Overview
The online world has changed drastically from when it first began. Today, everything you do- think communication, shopping, banking, watching movies, tax filing, buying stocks, studying- is done on the internet. And all these activities require some form of identification. This explosion of online services comes with its caveats. It is important to understand that our online data is probably as easily accessible to any hacker as it is to us. In a way, our private and sensitive information is always at stake.
What is Identity and Access Management?
Identity and Access Management (IAM) is a security discipline that ensures that the correct individual accesses the correct resources. It is a framework of business policies and technologies that facilitates the management of digital identities. Gartner describes IAM as a discipline that” enables the right individuals to access the right resources at the right times for the right reasons”. IAM acts as a gatekeeper that ensures that a user is what he claims (authentication) and is granted access (authorization) to resources based on his level of clearance and role.
Before we move any further, we must understand the meaning of authentication and authorization.
Authentication:
“Proves a user’s identity. It is based on the idea that each user will have unique information that sets them apart from other users to provide proof of identity. There are four primary types of authentication methods: static passwords that remain active until they are changed or expired; one-time passwords, such as codes delivered through SMS texts or tokens used for each access session; digital certificates; and biometric credentials.” (Source: Identity Management Institute)
All authentication methods require some verifiable information to be authenticated. There are three different categories of verifiable information:
- Knowledge factors: Things that you know.
- Possession factors: Things that you have.
- Inherence factors: Things that you are (biometric factors like fingerprints, retina scan etc.)
Some of the most well-known authentication methods are –
- Single-factor authentication (SFA): As the name suggests, the users are required to provide only one piece of information. This information could be anything- a password or a fingerprint. SFA should not be confused with Single Sign-on (SSO). Single sign-on provides users with the ability to log on once and be able to access resources or applications within the enterprise.
- Two-factor authentication (2FA): Users are required to provide two pieces of information. This added extra step acts as an additional security layer. Generally, the two types of required verifiable information are of different types. For example- the sign-on process might require a user to enter a username and password (Information they Know) and biometric identity, say fingerprint (Something they are). Or, the users are required to enter their credentials (Information they know) and then prove that their device is in their possession- by entering an OTP (Something they have).
- Multi-factor authentication (MFA): 2FA is also a part of MFA. In MFA, 2 or more different category factors are used to authenticate a sign-on.
- Risk-based authentication (RFA): Also called adaptive authentication, only asks for an MFA when it identifies a threat or risk. For example, a change in the user’s location or detection of malware on the user’s device.
It is not necessary that 2FA or MFA is more secure than SFA. Generally, passwords are the most common verifiable information used in SFA and are easily forgotten or compromised. On the other hand, fingerprints are also used in SFA and are one of the safest methods as they are difficult to fake. So, the security majorly depends on the type of factor/s used to authenticate.
Choosing an authentication method aims to strike a balance between security and user experience. MFA with fingerprint or facial recognition might seem like the safest bet, but it is expensive and requires the users to possess the technology to implement it. Similarly, SFA might be the best bet if not protecting sensitive information as it is cheaper and easier to implement.
Authorization:
“The process of granting or denying a user access to system resources once the user has been authenticated. The amount of information and services the user can access depends on the user’s authorization level.” Source: Identity Management Institute
Let us understand this with an example- Say you have to check into a hotel-
- First, you need to confirm that you are genuine, i.e., you are what you claim to be, by showing your identification papers.
- During check-in, you must prove that you have booked a room in that hotel by providing the booking name or number.
- After your authentication, you are provided with the keys to your room. Your assigned room determines what kind of services you can claim. For example, a person with a suite booking has a different level of services he can claim as compared to someone with a basic booking.
There are many ways to authorize access. 3 of the most common ones are:
- Role-based access control (RBAC): The user is granted access rights to the information that aligns with his role in the organization. The user has permission to access information that he needs to perform his job properly. Example: A junior marketing employee does not need access to IT Administration information to perform his job. He can only access the marketing tools and information.
- Attribute-based access control (ABAC): As the name suggests, ABAC uses attributes or characteristics to grant permissions. It is a fine-grained access management approach where access decisions are based on defined rules assigned to the user, action or environment. So, unlike RBAC, which defines roles that carry a specific set of privileges, ABAC can define rule sets that can evaluate many different attributes along with roles assigned. Example: A bank employee can only access the customer records via a particular branch IP address during regular working hours. In order to gain access from other branches, other security procedures must be followed.
- Policy-based access control (PBAC): In PBAC, the access permission is granted by user roles (similar to RBAC) and other additional attributes (similar to ABAC) combined with business logic. In large organizations, it becomes difficult to create roles for each access privilege; thus, additional attributes are used dynamically to grant access.
Importance of Identity Access Management (IAM)
Identity and access management (IAM) becomes even more necessary as cyber threats and privacy concerns rise. According to a Forrester estimate, 80% of data breaches are connected to compromised credentials like passwords, tokens, keys etc. IAM creates a security layer between the users and enterprise application, thus protecting against external and on-premises threats. It provides a centralized platform to manage identities for an enterprise and helps enforce access policies across devices and applications. It can also track user activities on company devices and enforce regulatory compliance.
(READ: Managing Enterprise Mobility Through Mobile Device Management)
Benefits of Identity Access Management (IAM)
The several benefits of IAM are as follows:
- Data Security: IAM helps prevent corporate information and login credentials proliferation and dissemination. Also, controlled user access allows enterprises to counter identity theft and illegal access issues.
- Effective Regulatory Compliance: IAM enables organizations to comply with various industry and government-mandated regulations. Thus, ensuring the security and privacy of the company data.
- Automation: Human errors can be reduced by automating low-priority and monotonous tasks such as reviewing access requests and workflow management. Also, in case of a policy update, access privileges can be managed and pushed through a centralized platform.
- Data Confidentiality: IAM allows restricted information access based on the role of the user. This segmentation minimizes fraudulent activities and gives managers a clear picture of their roles within an organization.
What is Centralized Identity Access Management (IAM)?
Organizations have a lot of personal data- of their employees, customers, potential clients etc. How this data is consolidated is very important and builds the basic security structure of an organization. The first step in this direction is a Centralized Identity management system.
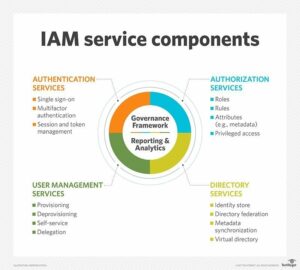
IAM can be deployed on-premises or provided by a third party through a cloud-based subscription model. According to TechTarget, IAM has four basic service components:
- Authentication Services
- Authorization Services
- User Management Services
- Directory Services
(READ- Security as a Service (SECaaS) – A Detailed Overview)
Centralized Identity management means all the IAM processes and data storage are done in one environment. This means users can access all the applications they need to work with the same set of credentials. As a trust relationship exists between the user, the organization and the partner applications/sites, with single sign-on in place, users can access the applications without signing into multiple accounts. For example, an enterprise can give its employees access to Salesforce, and with a single credential, the user can use the tools. This model is fundamentally built on bidirectional trust. Here the organization and Salesforce have a connection that they utilize to share information to authenticate and authorize the user.
This bi-directional trust model fundamentally differs from that used in Decentralized identity management systems. (Read more about Decentralized identity management systems)
Benefits of Centralized Identity Access Management (IAM)
- Efficient Threat Response: In case of a security breach, it is easier to identify and remedy the root cause in a centralized ID management system. As all the processes are centrally controlled, it is also cheaper and more efficient.
- Single Sign-on: In big organizations with various third-party tools, having different credentials for different applications gets cumbersome. As a result, users usually set a single id password combination for all their applications, which is both dangerous and easily compromised. Single Sign-on provides an easy way to deal with this issue. With SSO, users can use a single safe credential for all the applications and tools.
- Better Lifecycle Management: Granting and revoking access is much easier in Centralized identity management. This helps IT to have a better hold on the management system and aids in conducting thorough audits. The security team can also easily create, delete and modify policies through centralized monitoring.
The Future of Centralized IAM
A major drawback of Centralized IAM is that if the user credentials are compromised, the hacker can access all the information the user was privy to. This essentially means that since everything is centralized, there is a single point of failure. But strong authentication methods can easily help in mitigating the issue. HSC has been working on centralized IAM systems for quite some time now and believes its benefits far outweigh the negatives. Having a centralized IAM provides sound information security practices, efficient provisioning processes and a more accessible audit system. It also streamlines the new user creation, alteration, and termination processes. In short, Centralized IAM is here to stay.

Product Engineering Services Customized software development services for diverse domains
Quality Assurance End-to-end quality assurance and testing services
Managed Services Achieve scalability, operational efficiency and business continuity
Technology Consulting & Architecture Leverage the extensive knowledge of our Domain Experts