With the Internet of Things becoming mainstream and the ubiquity of wireless networks around us, IDC has predicted that there will be 41.6 billion connected IoT devices by 2025. With the immense benefits that the connected world brings to the consumers, it is also inviting attackers to continuously identify new exploits and hit techniques designed to circumvent the security around the IoT networks.
It is thus imperative to secure the IoT Networks considering the quantitative loss that it could bring to the industry and consumers. According to a study by MarketWatch, over the next five years, the Internet of Things (IoT) Security market will register a 32.5% CAGR in terms of revenue, the global market size will reach US$ 35900 million by 2024, from US$ 6630 million in 2019.
There are a plethora of tools and solutions available to detect attacks and block cyber-attacks such as firewalls, spam filters, and antimalware to protect endpoints across organizations, regardless of size or industry. However, another highly valuable security tool that is indispensable to ensure network security is the Intrusion Detection System also known as IDS in short.
What is an Intrusion Detection System?
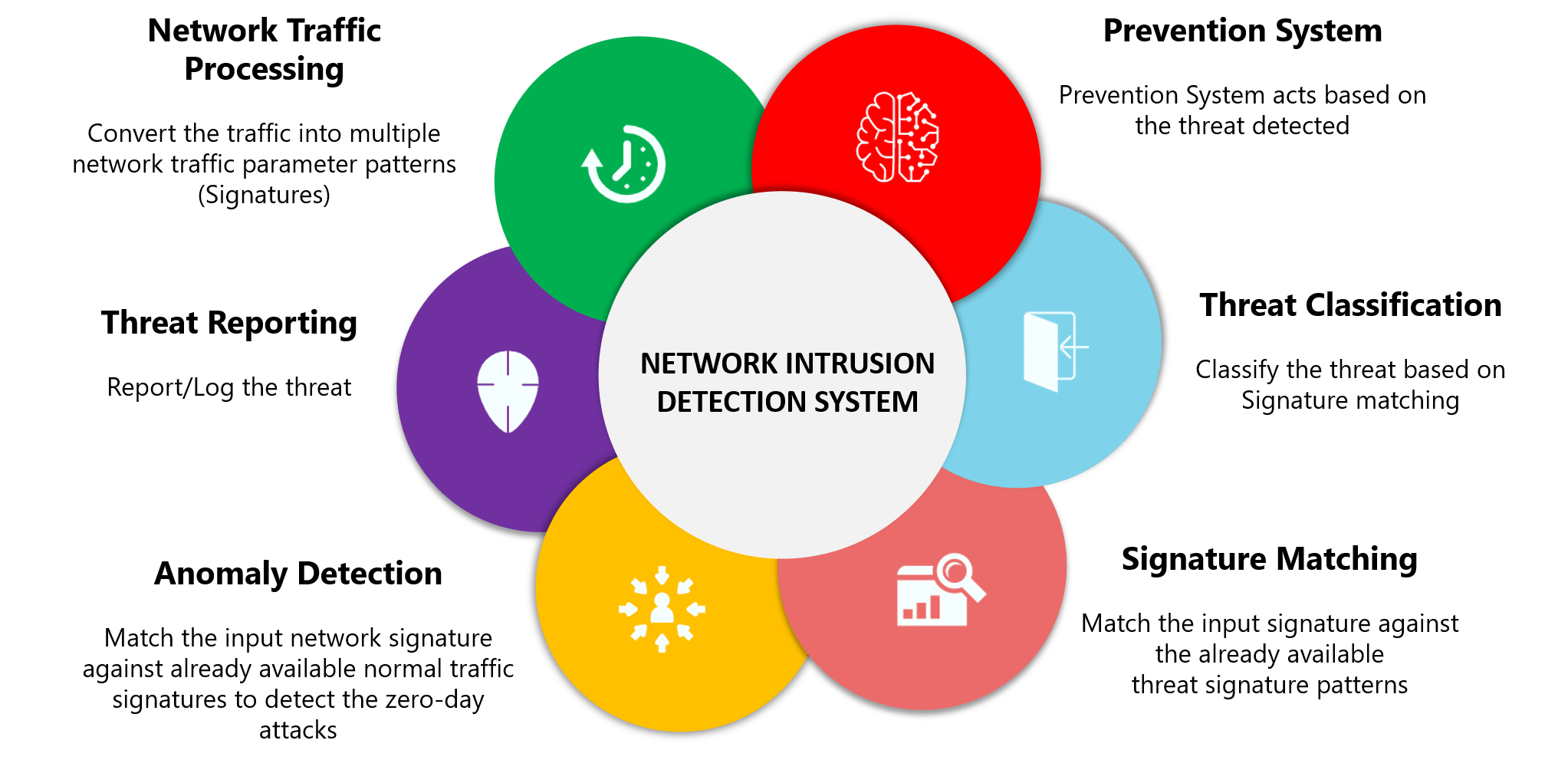
An Intrusion Detection System (IDS) is capable of detecting vulnerability within the network traffic and is placed out-of-band on the network infrastructure. IDS solutions utilize a TAP or SPAN port to analyze the inline traffic stream. They do not impact inline network performance since the IDS analyses a copy of the inline traffic stream. The IDS oversees the traffic and reports the findings to an administrator by sending alerts. However, IDS being a listen-only device, cannot automatically take action to prevent a detected attack or vulnerability from hitting the system.
The Alerting information generally includes information about the source address of the intrusion initiation, the target address, and the type of suspected attack.
With the adoption of intrusion detection software going mainstream, its function remains critical in modern enterprises and organizations. However, IDS solutions do not work as standalone solutions and need Intrusion Prevention Systems (IPS) for them to serve the purpose in totality.
Types of Intrusion Detection Systems
There are two types of intrusion detection systems based on the placement of IDS sensors within the network:
- Host-based IDS
- Network-based IDS
They are some smaller categories such as VM-based IDS, listing perimeter IDS, stack-based IDS, signature-based IDS, and anomaly-based IDS. For now, let us discuss the both major categories in greater detail.
1. Host-based IDS (HIDS):
Host-based intrusion detection systems are aimed at collecting information about malicious activity on a particular system, also called the host. Host-based agents, commonly referred to as sensors, are installed on the host machine to detect possible attacks. In a host-based IDS, each machine thus needs a separate sensor that works on collecting data about events taking place on the monitored host. A host-based sensor can also obtain data from other different sources such as system logs, OS processes logs, and contents of objects not reflected in standard OS audit and logging mechanisms.
2.Network-based IDS (NIDS)
The functioning of Network-based intrusion detection systems is different from host-based IDSs because the design philosophy differs completely.Network Intrusion Detection Systems scans network packets at the host/router level, audits the traffic packet information, and logs any malicious/suspicious packets into an alert log file with extended details. Today, network-based IDSs are becoming popular as the Internet is growing.
NIDS devices may be hardware or software-based systems and can attach to various network mediums like Ethernet, FDDI, etc.
NIDS systems are either signature-based, anomaly-based systems or hybrid.
Functioning of NIDS
NIDS build statistical models around the traffic they monitor and raise alerts on any traffic that deviates significantly from these baseline models.
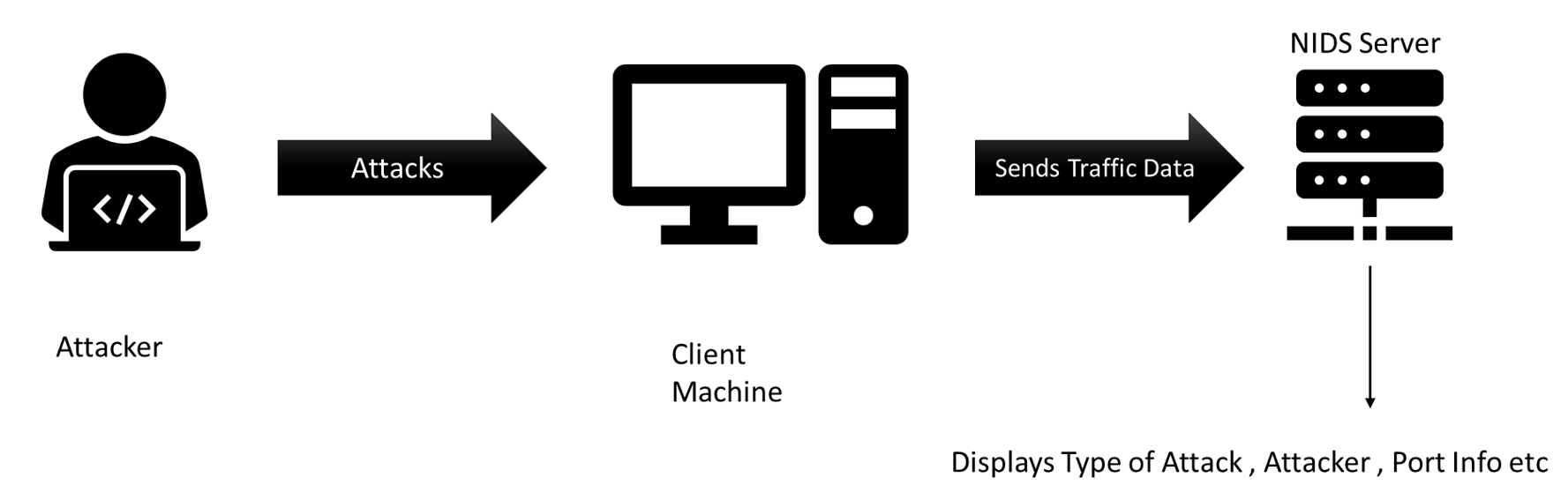
With the advancements in Machine Learning, it is now possible to detect the threat by training the system against the possible attack patterns and use that mind to separate out the threat from the normal traffic. The following figure below shows a typical mode of operation for NIDS. The network traffic is captured and sent to the NIDS server for the processing which detects the threat based on the machine learning model it is trained for.
There are multiple methods for detecting traffic anomalies. The most prevalent one involves checking traffic for compliance with various protocols standards such as TCP/IP for the underlying traffic, application layer protocols such as HTTP for Web traffic, SMTP for e-mail. Another model commonly used in NIDS systems revolves around monitoring models for user behavior and to raise alerts when the user deviates from the baseline patterns. Let us compare both these models for better understanding.
Though the model explained above looks sufficient, however, it is not. Some of the limitations of this model are:
- The Machine Learning model for which the system is trained might work for most of the scenarios but still, there might be cases where it might not be able to render the results with 100% accuracy.
- There are certain threats which the NIDS system is not trained to recognize. These are known as Zero-Day Attacks. The Zero Day attacks for which the system is not trained for would slip by silently without being detected
To overcome the following limitations, some of the architecture changes suggested within a NIDS system are:
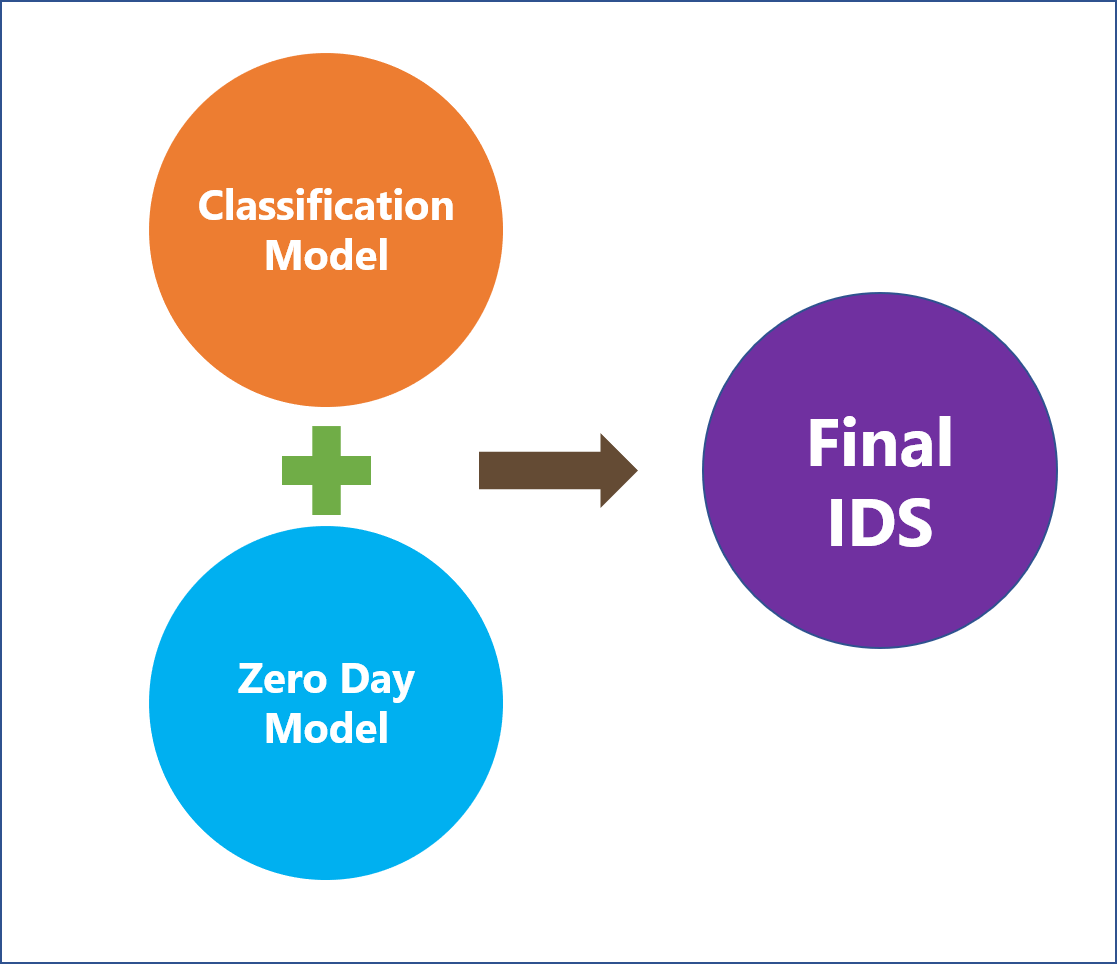
- Multiple Machine Learning models must be used to increase the chance of intrusion detection and application of a voting model on top of it. The threat must be detected and classified based on the consensus of the outcome of all the ML classification models.
- A logistic regression approach must be applied to detect the zero-day attacks in the system.
- The outcome from both the classification model and the regression model must be considered to finalize the details of the attack or whether there is an attack or not.
The following figure depicts this system:
The above model not only detects the security threats with greater accuracy it is also able to detect the zero-day attacks which is a significant positive from the traditional NIDS.

Product Engineering Services Customized software development services for diverse domains
Quality Assurance End-to-end quality assurance and testing services
Managed Services Achieve scalability, operational efficiency and business continuity
Technology Consulting & Architecture Leverage the extensive knowledge of our Domain Experts