Today’s rapidly evolving enterprise networks are highly reliant on cloud-based applications to run a multitude of business operations and use cases. In addition, the growth in the need for connectivity for business use-cases and mobile/remote users has resulted in the traditional enterprise network expanding beyond the network edge, thus bringing in a challenge to guard, secure and manage the network edge against vulnerabilities. Therefore, it is imperative for network owners to keep up with the latest security practices, frameworks and tools, rendering VPN-only solutions obsolete.
For enterprises to remain safeguarded and competitive in today’s network landscape with a zero-downtime, all network endpoints must be secured and managed with the same security and networking policies as their on-premises infrastructure. This is what makes a use case for SASE.
The term SASE was coined by Gartner in 2019 & was introduced to bring a highly customizable network with security services seamlessly stitched into the cloud platform. Secure Access Service Edge (SASE) architecture refers to a cybersecurity environment that brings advanced protection right out to the farthest edge of the network: the endpoints of users. In this SASE architecture definition, users are provided robust security features directly to their devices from the cloud, enabling them to connect securely from anywhere.
SASE brings multiple cloud-native security technologies together—Secure Web Gateway (SWG), Cloud Access Security Bearer (CASB), Zero Trust Network Access (ZTNA), and Firewall Solution as a service (FWaaS) with WAN capabilities to help users and systems connect securely to a service or any application; anytime and anywhere. Furthermore, since there is a need to make the ecosystem operations agile, the network’s security is delivered as a service from a centrally managed cloud.
With a 20% adoption rate expected by 2023, Gartner claimed that the demand for SASE capabilities would “redefine enterprise network and network security architecture and reshape the competitive landscape”. While SASE frameworks won’t be implemented in a day, the route to SASE is gaining speed and urgency. Another research by Palo Alto Networks and Gartner predicts the following for the future of SASE:
SASE network architecture provides cloud security to the farthest end of the network without relying on specific infrastructure. It allows users to connect directly to the cloud while enjoying security running on their devices. It enables a secure connection and decrease in latency resulting from backhauling to the data centre’s firewall.
SASE services involve cloud-hosted security, zero-trust network access (ZTNA) components, and network services components.
Cloud-hosted security enables devices to be independent of relying on security hosted on a physical data centre.
Zero trust network access (ZTNA), also known as the software-defined perimeter (SDP), is a set of technologies and functionalities that enable secure access to internal applications for remote users. It operates on an adaptive trust model, where trust is never implicit, and access is granted on a need-to-know, least-privileged basis defined by granular policies.
Network services components facilitate optimized path selection and application-based routing within the SASE architecture.
Traditionally, network security was hosted on the network edge within the corporate perimeter and the data centre, with all traffic routed through the data centre for validation and check. A SASE-based approach moves these capabilities to the cloud, where multiple applications are hosted, reducing the latency between the user and application and backhaul requirements.
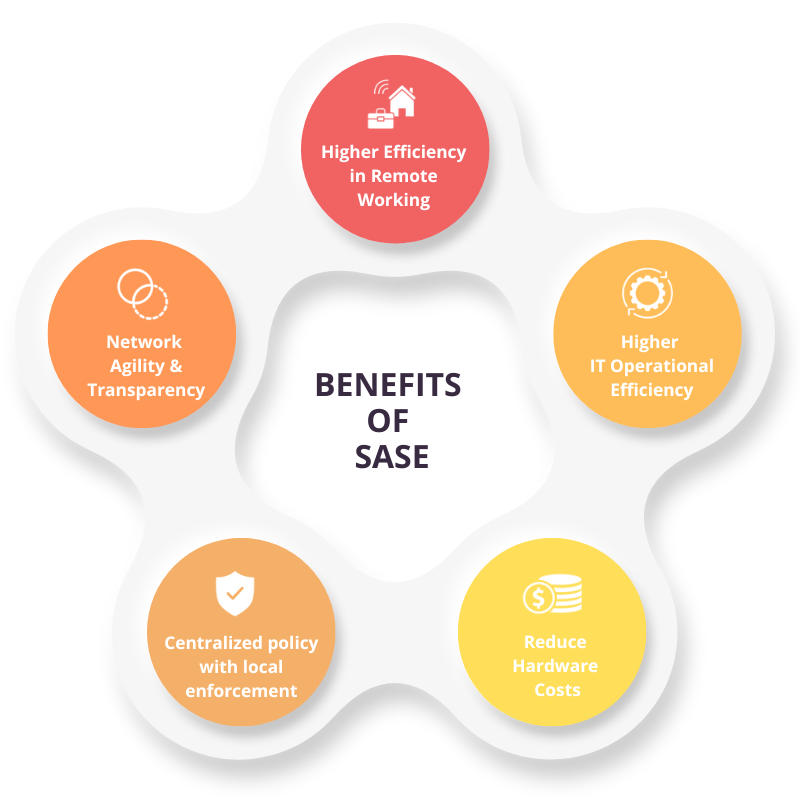
As time passes, organizations are gradually realizing the benefits of SASE, leading to an increase in adoption. However, while implementing SASE for your organization, you can also face some challenges.
Overcoming these SASE challenges will help ensure seamless and secure network operations in the long run.
Organizations need to analyze the existing IT infrastructure and make a roadmap to migrate/integrate the cloud environment. They also need to move away from the mindset of preferring traditional IT infrastructure over cloud.
Your IT workforce may not be skilled in handling hybrid cloud environments and implementing SASE. You need to do a thorough skill assessment of your workforce, provide them with training, or opt for a managed service provider (MSP). MSPs have a team of professionals skilled in SASE implementation, monitoring, and upgrade.
SASE requires the integration of various tools supplied by different vendors. It is imperative to find the right SASE vendors or solution providers to ensure a smooth transition to SASE.
In most organizations, the network and security teams work as different entities. However, the implementation of Secure Access Service Edge requires both teams to work on the same page. Otherwise, there can be issues with security or performance.
Implementing SASE can lead to bandwidth issues if the network architecture is not properly optimized. As a result, users can experience latency, leading to a dip in productivity.
The SASE framework comprises various components, as discussed in the earlier section. All the components can be served by multiple tools available in the market. However, sometimes, integrating multiple tools can lead to compatibility issues.
While implementing a SASE architecture, data privacy and compliance is a major challenge. This is because users operate in a hybrid work environment, which means that data needs to pass through multiple touchpoints, even geographies.
Ensuring a seamless and uniform user experience is quite a challenge as SASE architecture involves multiple users operating from different regions. Hence, bandwidth can be an issue in this regard.
Juniper Networks recommends the following approach for the adoption of SASE:
The focus on adopting SASE and Secure Edge within organizations continues to grow, pushing a broader basket of integrated cloud-based cybersecurity technologies into a more consumable form. The industry would see some consolidation, integration, and M&A in the SASE market over the years as the number of players in the SASE market continue to grow globally. SASE promises to handle vulnerabilities at every network edge: data centre, branch, cloud & mobile. Currently, these solutions come from varied vendors; hence interoperability will be critical for all vendors. This could also drive their consolidation approaches from enterprises & demand for the adoption of unified SASE solutions.